AlwaysUp Web Service version 13.2 was published on February 4 2022.
This new release — which is fully certified for Windows 11 and Windows Server 2022 — includes a handful of improvements and fixes. Consequently, please upgrade at your earliest convenience.
But of all the new features, the ability to work with reverse proxy servers is the most impactful. So let’s dig into that capability today…
What is a Reverse Proxy? Why would I use one?
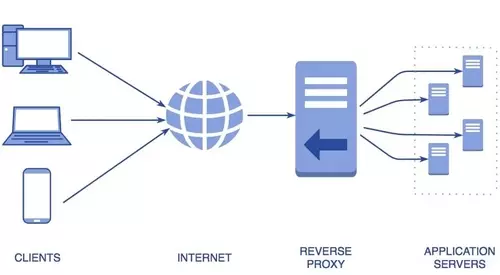
A reverse proxy is an application that sits in front of one or more back-end services and enables users to access those services from a single location. In doing so, the proxy “hides” the location and other details of the back-end services from the users.
For example, let’s take Acme Inc — an IT company that operates three web services. Acme hosts each web service on its own internal server, accessible at the following URLs:
http://10.0.0.104/get-menu
http://10.0.0.105/wsapi/v2/create-booking
http://10.0.0.106:8880/daily-report.php
Because the web services are deployed on the company’s private network (10.x.x.x), none of them are accessible from the Internet. Therefore, customers cannot get menus, create bookings or view reports. And Acme wants to change that.
To make the web services accessible to its customers, Acme introduces a reverse proxy. Their IT team deploys a new server and configures it securely at https://api.acme.com.
Now customers can visit all three services under the same umbrella, at:
https://api.acme.com/api/food/get-menu
https://api.acme.com/api/reservations/wsapi/v2/create-booking
https://api.acme.com/api/reports/daily-report.php
As a result, with the help of the reverse proxy, Acme has provided a valuable service to it’s customers — all with security, scalability and usability in mind!
Reverse Proxy configuration
In order for AlwaysUp Web Service to work with a reverse proxy, the proxy must pass the following headers in each request it forwards:
X-Base-URL: The path/location where the proxy server serves AlwaysUp Web Service. For example, if AlwaysUp Web Service should be available at http://proxy.acme.com/alwaysup-web-service/, the X-Base-URL value should be /alwaysup-web-service/.
X-Forwarded-For: The originating IP address of the client connecting the proxy server. This allows AlwaysUp Web Service to track the true source of the request.
Reverse Proxy setup with NGINX
Let’s review an example with NGINX — a popular web server that supports reverse proxy configuration.
Acme hosts AlwaysUp Web Service at http://10.10.0.1:8585. In addition, its Internet-facing proxy server is accessible at http://proxy.acme.com.
To make AlwaysUp Web Service available to users outside of Acme’s internal network, the server section of the proxy’s NGINX configuration file looks like this:
server {
listen 80;
location /alwaysup/ {
proxy_set_header X-Base-URL /alwaysup-web-service/;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://10.10.0.1:8585/;
}
}
With that setup in place, Acme’s users can access AlwaysUp Web Service at
SSL Configuration
Setup is a tad more complicated when working with HTTPS. Assuming the same conditions as above, here is Acme’s NGINX configuration for the SSL scenario:
server {
listen 443 ssl;
ssl_certificate "ssl/certificate.pem";
ssl_certificate_key "ssl/certificate-key.pem";
ssl_protocols TLSv1.2;
location /alwaysup/ {
proxy_set_header X-Base-URL /alwaysup/;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://10.10.0.1:8585/;
}
}
Feel free to use the self-signed certificate files distributed with AlwaysUp Web Service. They are available in the “certificates” sub-folder of the installation directory.
A sample NGINX configuration file (with server sections for both the HTTP and HTTPS scenarios) is available at our website.
Enjoy!






 Uninstall the system extension
Uninstall the system extension