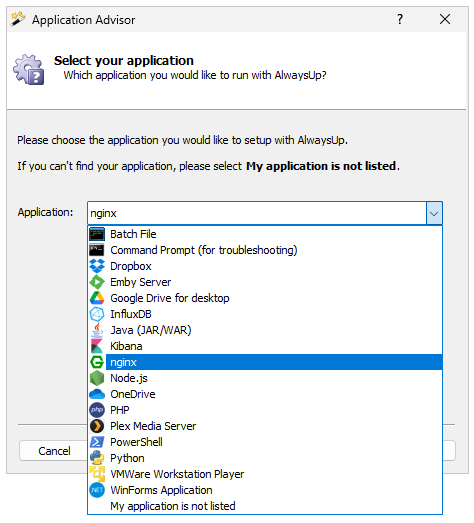
We have an important service and only Admins are allowed to use it. If there’s an issue and the service needs to be restarted, regular users who aren’t in the Administrators group have to put in a ticket.
To reduce the support calls, we’d like to give certain regular users the capability to see if the service is running and restart it if it isn’t. What’s the best way to do that?
— Alex
Hi Alex, thanks for reaching out. We can definitely help you tackle this issue with our free Windows Service utilities. It should only take you a few minutes to implement the following two-step process and you’ll be good to go.
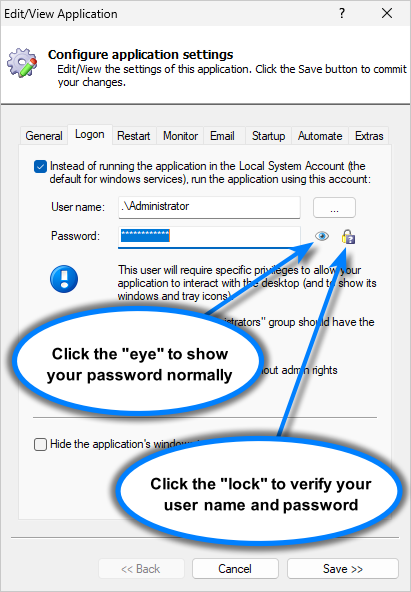
Step 1: Use Service Security Editor to allow the user to start or stop the Windows Service
By default, only administrators can manage a Windows Service. And more often than not, regular users are summarily rejected with an “access denied” error when they try to start or stop the service because they don’t have the necessary rights. That’s the first problem we have to fix.
For example, we have a regular user named “Hazel Jones” on our system. Because she’s not in the Administrators group, her attempts to stop the Print Spooler service using the NET command are consistently rebuffed:
Your team’s probably in the same situation as Hazel.
So here’s what you should do to allow your users to control your Windows Service. We’ll use Hazel and the Spooler service to illustrate:
Download our free Service Security Editor program.
Start Service Security Editor.
Select your Windows Service from the list:
Click the Open button.
As you can see in the Service Security Settings window that comes up, only Administrators have full control over the service. For example, Hazel was nowhere to be found in our list.
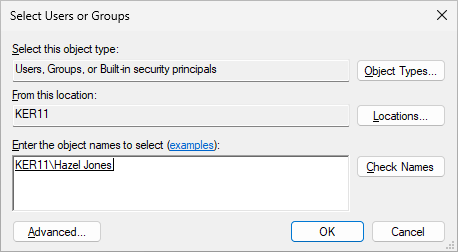
Click the Add button to add the non-admin account:
Enter the account name and click OK:
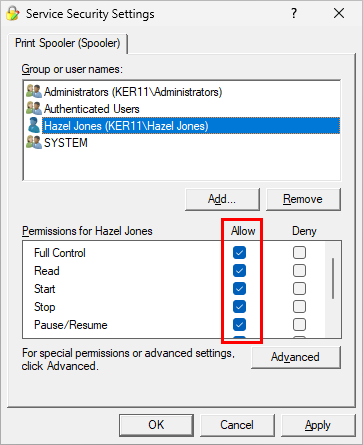
Back in the Service Security Settings window, select the newly added user in the top panel. Afterwards, ensure that the user has all the rights you would like to give them in the lower panel.
For example, we granted Hazel full permissions over Spooler. She’ll be able to start, stop or restart the service whenever she likes:
Click OK to save your changes. And exit Service Security Editor since we’re done with that program.
At this point, your non-admin user should be able to control your Windows Service. The NET command should succeed now, as it did here for Hazel:
But even though your user can now stop the service, that alone won’t make it easy for them to do so! The truth is that very few folks are comfortable invoking the NET command from a prompt, and it’s almost as painful to explain how to drive the Services application. We can do better — and that’s the focus of the next step.
Step 2: Have your user install ServiceTray, to make it easy to work with the Windows Service
In this second part of the solution, your non-admin user will install another of our popular, free programs, ServiceTray. This helpful tool will make it obvious when the service is running — and allow the user to easily stop, start or restart the service whenever there’s trouble.
To set this up, your regular user should:
Download and install ServiceTray. It should only take a couple of minutes to breeze through the straightforward process.
Start ServiceTray.
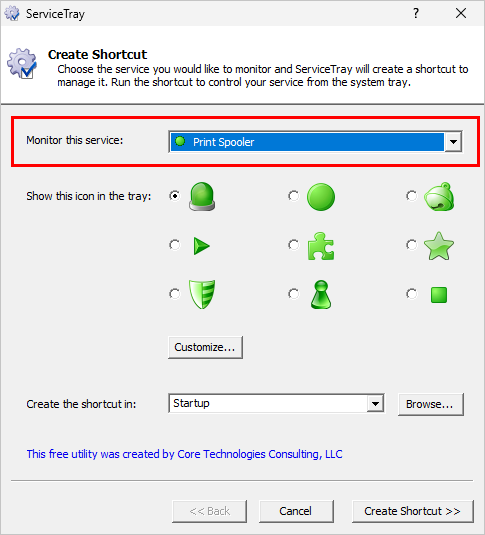
In the window that comes up, choose the Windows Service from the drop-down at the top. For example, Hazel selected the Print Spooler service here:
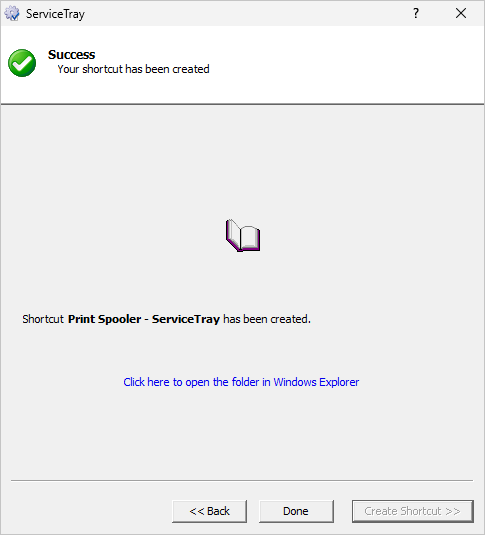
Next, click the Save button. That will create a shortcut in your Windows Startup Folder — the location holding the applications that Windows launches whenever you log in:
Click the Done button to close ServiceTray.
The next time the user logs in, Windows will start ServiceTray automatically. After a few seconds, a new icon will show up in the “tray area” on the right of the Windows taskbar:
If the icon doesn’t show up in the tray area, they may need to change their Windows taskbar settings to show the icon. Hazel had to make that change:
Using ServiceTray
A quick look at the tray icon will tell the user if the service is running or not. The color of the icon will be:
Green when the service is running (as shown above).
Red when the service is stopped:
Yellow when the service is starting, stopping or in any other state:
To take some action on the service, click the icon to summon ServiceTray’s menu:
From there you can start, stop, restart or even get information about the service — all with a click of the mouse.
Hope this helps!











![OneDrive Version 23.48: Trouble Running in Session 0 [RESOLVED]](https://www.coretechnologies.com/blog/wp-content/uploads/onedrive-error-150x150-1.webp)